本地侦查思路
在成功的利用之后,我们已经拿到了服务器本地的访问了,根据服务器配置的不同,此时我们可能已经是最高权限了,也可能是低权限用户。我们需要充分利用现有的访问,对本地信息进行详尽的侦查,包括但不局限于网络配置、本地文件、用户和群组、分配的权限、系统版本、存储的凭证等。
对于提权,不一定是必要的,但是提权能让我们访问到更多的信息,从而提高入侵更多主机的成功率。我这里强调一个思想:侦查的目标不是 (本地)提权,而(本地)提权的目标是侦查更多信息。对于企业的域网络,我们即便拿到了当前主机的最高权限,也是远远不够的,所做的一切都是为了能将口子撕地更大。我们需要摆脱打靶机的思维定势,即用提权工具跑一下,找到提权向量然后任务完成。
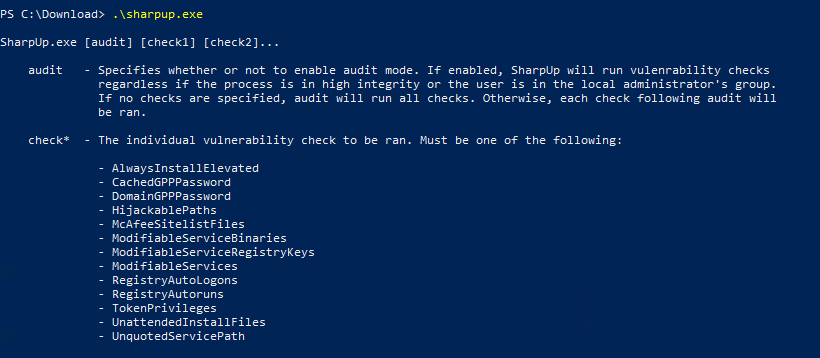
常见且好用的提权与侦查工具有 WinPEAS (https://github.com/carlospolop/PEASS-ng/tree/master/winPEAS/winPEASexe),SharpUp (https://github.com/GhostPack/SharpUp),Seatbelt(https://github.com/GhostPack/Seatbelt) 等。在我们做靶场练习的时候,这些工具的作用是帮助我们寻找提权路径,但实际上,这些工具更强大的功能在于本地侦查。如果不借助这些工具,同学们可能会有些不知所措,不知道有哪些信息需要搜集,怎么对需要搜集的信息分门别类。
作为网络安全专家,我们不能依赖于工具,但是可以参考这些工具的思路,再怎么说这些工具也是集思广益后编写的,也得到了普遍的认可。我们先以最轻量级的 SharpUp 来举例:
SharpUp 的功能主要建立在特权提升上,但如果例如 CachedGPPPassword,DomainGPPPassword 等选项能返回有效结果,即便已经获得了最高权限,对我们依旧是有帮助的。对于 SharpUp 所检查的项目,总结一下如下:
1:本地提权类。AlwaysInstalledElevated、服务提权、Token权限、权限配置不当的路径等。
2:凭证类。CachedGPPPassword,DomainGPPPassword,RegistryAutoLogons 等。如果能得到明文凭证,无论对本地提权,还是域内提权、横向移动都可能有帮助。因此,即便已经拿到了本地最高特权,也要检查一下这些选项。
我们接下来查看 WinPEAS 的检查项目
System Information
Basic System info information
Use Watson to search for vulnerabilities
Enumerate Microsoft updates
PS, Audit, WEF and LAPS Settings
LSA protection
Credential Guard
WDigest
Number of cached cred
Environment Variables
Internet Settings
Current drives information
AV
Windows Defender
UAC configuration
NTLM Settings
Local Group Policy
Applocker Configuration & bypass suggestions
Printers
Named Pipes
AMSI Providers
SysMon
.NET Versions
Users Information
Users information
Current token privileges
Clipboard text
Current logged users
RDP sessions
Ever logged users
Autologin credentials
Home folders
Password policies
Local User details
Logon Sessions
Processes Information
Interesting processes (non Microsoft)
Services Information
Interesting services (non Microsoft) information
Modifiable services
Writable service registry binpath
PATH Dll Hijacking
Applications Information
Current Active Window
Installed software
AutoRuns
Scheduled tasks
Device drivers
Network Information
Current net shares
Mapped drives (WMI)
hosts file
Network Interfaces
Listening ports
Firewall rules
DNS Cache (limit 70)
Internet Settings
Windows Credentials
Windows Vault
Credential Manager
Saved RDP settings
Recently run commands
Default PS transcripts files
DPAPI Masterkeys
DPAPI Credential files
Remote Desktop Connection Manager credentials
Kerberos Tickets
Wifi
AppCmd.exe
SSClient.exe
SCCM
Security Package Credentials
AlwaysInstallElevated
WSUS
Browser Information
Firefox DBs
Credentials in firefox history
Chrome DBs
Credentials in chrome history
Current IE tabs
Credentials in IE history
IE Favorites
Extracting saved passwords for: Firefox, Chrome, Opera, Brave
Interesting Files and registry
Putty sessions
Putty SSH host keys
SuperPutty info
Office365 endpoints synced by OneDrive
SSH Keys inside registry
Cloud credentials
Check for unattended files
Check for SAM & SYSTEM backups
Check for cached GPP Passwords
Check for and extract creds from McAffe SiteList.xml files
Possible registries with credentials
Possible credentials files in users homes
Possible password files inside the Recycle bin
Possible files containing credentials (this take some minutes)
User documents (limit 100)
Oracle SQL Developer config files check
Slack files search
Outlook downloads
Machine and user certificate files
Office most recent documents
Hidden files and folders
Executable files in non-default folders with write permissions
WSL check
Events Information
Logon + Explicit Logon Events
Process Creation Events
PowerShell Events
Power On/Off Events
Additional (slower) checks
LOLBAS search
run linpeas.sh in default WSL distributionWinPEAS 检查的内容更加丰富和延伸,总结一下,有这么几类
1:系统信息。包含了系统版本、补丁、本地安全控制、计算机设置等。
2:用户信息。包含了用户信息、用户特权、活跃会话、自动登陆等。
3:进程信息
4:服务信息。主要用于提权。
5:应用信息。包含了活跃窗口、安装的软件、驱动、计划任务等。
6:网络信息。包含了开放端口、网卡接口、DNS缓存、共享目录等。
7:Windows 凭证。包含了仓库、凭证管理器、DPAPI、Wifi 密码、Kerberos 票据等。
8:浏览器信息。包含了常见浏览器的缓存凭证、收藏夹等。
9:文件和注册表信息。包含了系统敏感文件和注册表项、常见应用 (如 PuTTY) 的重要文件等
10:事件信息与其他
我们手动枚举的时候,可以借鉴 WinPEAS 的检查列表。
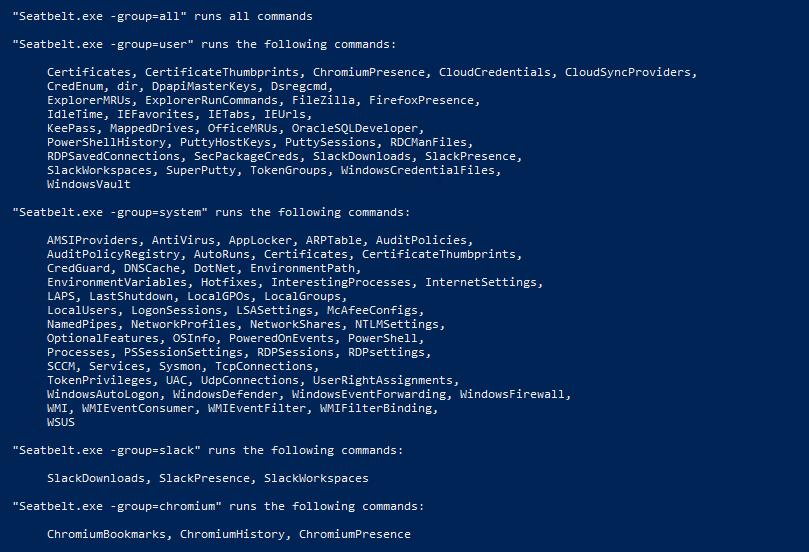
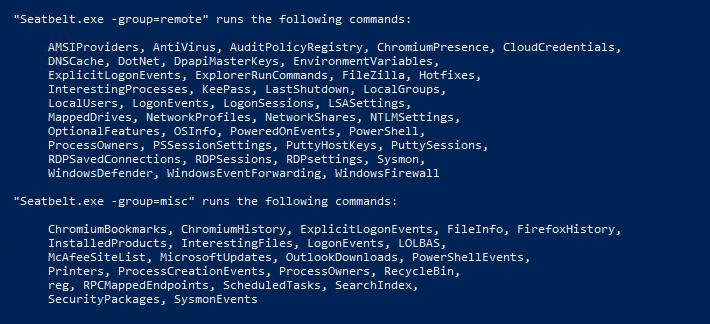
最后,我们一起看看 SeatBelt 的枚举思路:
Available commands (+ means remote usage is supported):
+ AMSIProviders - Providers registered for AMSI
+ AntiVirus - Registered antivirus (via WMI)
+ AppLocker - AppLocker settings, if installed
ARPTable - Lists the current ARP table and adapter information (equivalent to arp -a)
AuditPolicies - Enumerates classic and advanced audit policy settings
+ AuditPolicyRegistry - Audit settings via the registry
+ AutoRuns - Auto run executables/scripts/programs
Certificates - Finds user and machine personal certificate files
CertificateThumbprints - Finds thumbprints for all certificate store certs on the systen
+ ChromiumBookmarks - Parses any found Chrome/Edge/Brave/Opera bookmark files
+ ChromiumHistory - Parses any found Chrome/Edge/Brave/Opera history files
+ ChromiumPresence - Checks if interesting Chrome/Edge/Brave/Opera files exist
+ CloudCredentials - AWS/Google/Azure/Bluemix cloud credential files
+ CloudSyncProviders - All configured Office 365 endpoints (tenants and teamsites) which are synchronised by OneDrive.
CredEnum - Enumerates the current user's saved credentials using CredEnumerate()
+ CredGuard - CredentialGuard configuration
dir - Lists files/folders. By default, lists users' downloads, documents, and desktop folders (arguments == [directory] [maxDepth] [regex] [boolIgnoreErrors]
+ DNSCache - DNS cache entries (via WMI)
+ DotNet - DotNet versions
+ DpapiMasterKeys - List DPAPI master keys
Dsregcmd - Return Tenant information - Replacement for Dsregcmd /status
EnvironmentPath - Current environment %PATH$ folders and SDDL information
+ EnvironmentVariables - Current environment variables
+ ExplicitLogonEvents - Explicit Logon events (Event ID 4648) from the security event log. Default of 7 days, argument == last X days.
ExplorerMRUs - Explorer most recently used files (last 7 days, argument == last X days)
+ ExplorerRunCommands - Recent Explorer "run" commands
FileInfo - Information about a file (version information, timestamps, basic PE info, etc. argument(s) == file path(s)
+ FileZilla - FileZilla configuration files
+ FirefoxHistory - Parses any found FireFox history files
+ FirefoxPresence - Checks if interesting Firefox files exist
+ Hotfixes - Installed hotfixes (via WMI)
IdleTime - Returns the number of seconds since the current user's last input.
+ IEFavorites - Internet Explorer favorites
IETabs - Open Internet Explorer tabs
+ IEUrls - Internet Explorer typed URLs (last 7 days, argument == last X days)
+ InstalledProducts - Installed products via the registry
InterestingFiles - "Interesting" files matching various patterns in the user's folder. Note: takes non-trivial time.
+ InterestingProcesses - "Interesting" processes - defensive products and admin tools
InternetSettings - Internet settings including proxy configs and zones configuration
+ KeePass - Finds KeePass configuration files
+ LAPS - LAPS settings, if installed
+ LastShutdown - Returns the DateTime of the last system shutdown (via the registry).
LocalGPOs - Local Group Policy settings applied to the machine/local users
+ LocalGroups - Non-empty local groups, "-full" displays all groups (argument == computername to enumerate)
+ LocalUsers - Local users, whether they're active/disabled, and pwd last set (argument == computername to enumerate)
+ LogonEvents - Logon events (Event ID 4624) from the security event log. Default of 10 days, argument == last X days.
+ LogonSessions - Windows logon sessions
LOLBAS - Locates Living Off The Land Binaries and Scripts (LOLBAS) on the system. Note: takes non-trivial time.
+ LSASettings - LSA settings (including auth packages)
+ MappedDrives - Users' mapped drives (via WMI)
McAfeeConfigs - Finds McAfee configuration files
McAfeeSiteList - Decrypt any found McAfee SiteList.xml configuration files.
MicrosoftUpdates - All Microsoft updates (via COM)
NamedPipes - Named pipe names, any readable ACL information and associated process information.
+ NetworkProfiles - Windows network profiles
+ NetworkShares - Network shares exposed by the machine (via WMI)
+ NTLMSettings - NTLM authentication settings
OfficeMRUs - Office most recently used file list (last 7 days)
OneNote - List OneNote backup files
+ OptionalFeatures - List Optional Features/Roles (via WMI)
OracleSQLDeveloper - Finds Oracle SQLDeveloper connections.xml files
+ OSInfo - Basic OS info (i.e. architecture, OS version, etc.)
+ OutlookDownloads - List files downloaded by Outlook
+ PoweredOnEvents - Reboot and sleep schedule based on the System event log EIDs 1, 12, 13, 42, and 6008. Default of 7 days, argument == last X days.
+ PowerShell - PowerShell versions and security settings
+ PowerShellEvents - PowerShell script block logs (4104) with sensitive data.
+ PowerShellHistory - Searches PowerShell console history files for sensitive regex matches.
Printers - Installed Printers (via WMI)
+ ProcessCreationEvents - Process creation logs (4688) with sensitive data.
Processes - Running processes with file info company names that don't contain 'Microsoft', "-full" enumerates all processes
+ ProcessOwners - Running non-session 0 process list with owners. For remote use.
+ PSSessionSettings - Enumerates PS Session Settings from the registry
+ PuttyHostKeys - Saved Putty SSH host keys
+ PuttySessions - Saved Putty configuration (interesting fields) and SSH host keys
RDCManFiles - Windows Remote Desktop Connection Manager settings files
+ RDPSavedConnections - Saved RDP connections stored in the registry
+ RDPSessions - Current incoming RDP sessions (argument == computername to enumerate)
+ RDPsettings - Remote Desktop Server/Client Settings
RecycleBin - Items in the Recycle Bin deleted in the last 30 days - only works from a user context!
reg - Registry key values (HKLM\Software by default) argument == [Path] [intDepth] [Regex] [boolIgnoreErrors]
RPCMappedEndpoints - Current RPC endpoints mapped
+ SCCM - System Center Configuration Manager (SCCM) settings, if applicable
+ ScheduledTasks - Scheduled tasks (via WMI) that aren't authored by 'Microsoft', "-full" dumps all Scheduled tasks
SearchIndex - Query results from the Windows Search Index, default term of 'passsword'. (argument(s) == <search path> <pattern1,pattern2,...>
SecPackageCreds - Obtains credentials from security packages
SecurityPackages - Enumerates the security packages currently available using EnumerateSecurityPackagesA()
Services - Services with file info company names that don't contain 'Microsoft', "-full" dumps all processes
+ SlackDownloads - Parses any found 'slack-downloads' files
+ SlackPresence - Checks if interesting Slack files exist
+ SlackWorkspaces - Parses any found 'slack-workspaces' files
+ SuperPutty - SuperPutty configuration files
+ Sysmon - Sysmon configuration from the registry
+ SysmonEvents - Sysmon process creation logs (1) with sensitive data.
TcpConnections - Current TCP connections and their associated processes and services
TokenGroups - The current token's local and domain groups
TokenPrivileges - Currently enabled token privileges (e.g. SeDebugPrivilege/etc.)
+ UAC - UAC system policies via the registry
UdpConnections - Current UDP connections and associated processes and services
UserRightAssignments - Configured User Right Assignments (e.g. SeDenyNetworkLogonRight, SeShutdownPrivilege, etc.) argument == computername to enumerate
WifiProfile - Enumerates the saved Wifi profiles and extract the ssid, authentication type, cleartext key/passphrase (when possible)
+ WindowsAutoLogon - Registry autologon information
WindowsCredentialFiles - Windows credential DPAPI blobs
+ WindowsDefender - Windows Defender settings (including exclusion locations)
+ WindowsEventForwarding - Windows Event Forwarding (WEF) settings via the registry
+ WindowsFirewall - Non-standard firewall rules, "-full" dumps all (arguments == allow/deny/tcp/udp/in/out/domain/private/public)
WindowsVault - Credentials saved in the Windows Vault (i.e. logins from Internet Explorer and Edge).
+ WMI - Runs a specified WMI query
WMIEventConsumer - Lists WMI Event Consumers
WMIEventFilter - Lists WMI Event Filters
WMIFilterBinding - Lists WMI Filter to Consumer Bindings
+ WSUS - Windows Server Update Services (WSUS) settings, if applicable以上是多达 113 项的检查列表,SeatBelt 也支持分类枚举,例如针对系统的、针对用户的、针对 Chromium 浏览器的、可远程枚举等分类。
简单查看与分析了这 3 款本地侦查与提权的工具后,我们大概知道了本地侦查阶段需要搜集的信息都可以有哪些。其实,这份检查列表还是很长的,但我们可以根据目标进行灵活调节,把握好优先级。例如,相比服务器,我们能从个人主机上获得更多的浏览器、第三方应用的敏感信息与文件。
未来补充:https://trustedsec.com/blog/walking-the-tightrope-maximizing-information-gathering-while-avoiding-detection-for-red-teams